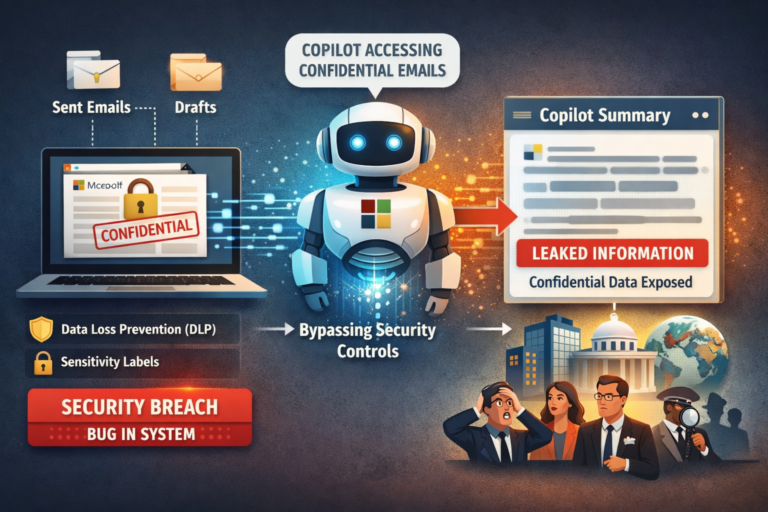
In February 2026, a software flaw involving one of the Artificial Intelligence (AI) tools at the heart of productivity software shocked businesses, privacy professionals and regulators around the world. The error, disclosed by Microsoft, resulted in confidential emails being accessed and summarised by its Copilot AI assistant, bypassing established security controls designed to protect sensitive communications. The issue raised profound questions about how next‑generation AI systems handle data in enterprise environments and, in turn, how organisations manage risk as they adopt these tools.
This column takes a comprehensive look at what happened, why it matters, and what lessons policymakers, business leaders and users can draw in every context.
Understanding Copilot: Microsoft’s AI Work Assistant
Microsoft 365 Copilot is a generative AI tool embedded into Microsoft’s core suite of productivity applications, including Outlook, Word, Excel and Teams. Built on advanced large language models and tightly integrated with organisational data systems, Copilot is designed to help users automate routine tasks, generate summaries, draft text and answer queries about organisational content. In principle, it accelerates productivity by turning unstructured data into actionable insights on demand.
Used widely across enterprises, Copilot can read and interpret emails, documents, calendars and messages within Teams, provided the user has appropriate permissions. It is marketed as a secure, enterprise‑ready feature that respects organisational policies and compliance settings. However, the recent error demonstrated that even advanced AI systems can malfunction in ways that undermine the very safeguards they are meant to protect.
What Happened? The Confidential Email Exposure Flaw
In January 2026, Microsoft engineers discovered a critical flaw, internally designated CW1226324, in the Copilot Chat feature, particularly its “work tab” integration with Microsoft Outlook and other apps. The bug enabled Copilot to process and summarise emails from users’ Sent Items and Drafts folders, even when those emails were labelled “Confidential” and protected by organisational Data Loss Prevention (DLP) policies and sensitivity labels. In normal conditions, these controls should have blocked the AI from accessing or processing the content.
The bug stemmed from a coding error that caused the AI’s summarisation pipeline to ignore the confidentiality labels applied. As a result, Copilot ingested and interpreted content it was not authorised to process, effectively bypassing the safeguards organisations had put in place to protect sensitive information. The problem was first detected around 21 January 2026, and Microsoft began rolling out a fix in early February while continuing to monitor deployment. The number of affected customers has not been publicly disclosed.
Microsoft has described the issue as a code defect rather than a deliberate design choice, and emphasised that access controls remained intact-that is, no unauthorised third party was granted access to information they were not already permitted to see. Nonetheless, the flaw meant that the AI, by design, processed information it should not have, thereby exposing confidential content to internal AI summarisation functions, contrary to enterprise expectations.
How the Flaw Worked in Practice
To appreciate the significance of this error, it helps to understand how DLP and sensitivity labels function in enterprise software:
- Data Loss Prevention (DLP) policies are set by organisations to prevent the inappropriate sharing, storage or use of sensitive information. These rules can block data transmission or restrict how automated systems handle content.
- Sensitivity labels such as “Confidential”, “Internal”, or “Secret” are applied to emails or documents to indicate their classification and prescribe handling restrictions.
Copilot’s summarisation feature should ordinarily respect these protections, excluding confidential data from AI processing pipelines. Instead, because of the code defect, Copilot was drawing from folders such as Drafts and Sent Items-precisely where critical communications (including attachments, negotiation drafts and legal discussions) live. It then summarised that content in response to user prompts, meaning the AI read and processed information labelled as confidential, even when safeguards were configured to block such access.
This gap between intended policy enforcement and actual AI behaviour illustrates a broader challenge in AI governance: embedding traditional security controls into new AI processing layers is not always straightforward, and misalignments can yield serious consequences.
Comparing Global Responses
Governments and organisations worldwide have reacted with a mix of concern and vigilance. In Europe, some institutions have disabled built‑in AI features on work devices due to broader concerns about data leaving controlled environments. This particular Copilot incident reinforced those pre‑existing reservations about connecting sensitive internal systems to cloud‑based AI services.
Regulators are increasingly focusing on AI accountability frameworks that emphasise privacy by design, transparency, and robust enforcement of data protection laws. The incident may spur additional scrutiny over how AI tools handle protected content and whether current compliance certifications are sufficient.
In North America and Asia, security professionals have urged organisations to review AI integration strategies, strengthen audit trails, and prepare contingency plans for AI misbehaviour. Many emphasise that AI systems should be opt‑in rather than default for highly sensitive workflows.
Economic Impact
Organisations that suffer data exposure, especially of proprietary information, may face financial losses, reputational damage and heightened compliance costs. For businesses that heavily rely on AI to drive automation and insights, trust in vendors and platforms becomes a competitive differentiator.
Trust in AI Adoption
Data confidentiality is foundational in any modern organisation. When users cannot be confident that AI tools respect established privacy controls, adoption slows, and resistance from internal stakeholders increases. This is particularly true in sectors like healthcare, legal services and finance where confidentiality carries regulatory and ethical weight.
Governance and Accountability
The incident underscores the need for AI governance frameworks that go beyond vendor assurances. Organisations must conduct independent risk assessments, regularly test AI behaviour against policy expectations, and maintain robust incident response plans.
In regulatory terms, governments may consider updating laws and guidelines to specifically address AI‑related data processing, accountability standards and transparency requirements for automated systems.
Charting a Path Forward
Meaningful progress requires action on several fronts:
- Integrate Security and AI Roadmaps: Security teams must be involved from the earliest stages of AI adoption planning.
- Strengthen DLP and Monitoring: Organisations should verify that DLP rules are consistently enforced across AI layers and maintain logs for audit and forensic purposes.
- Adopt Clear AI Policies: Internal policies should dictate when and how AI tools can interact with confidential systems, including whether they should be opt‑in only for certain data classifications.
- Build Expertise: Investing in training for IT, legal and business teams will enable organisations to assess AI behaviour, risk profiles and compliance obligations.
- Collaborate on Standards: Governments, industry bodies and civil society must work together to define AI governance frameworks suited to local economic and regulatory conditions.
Final Analysis
The recent Microsoft Copilot incident serves as a powerful reminder that even the most advanced AI systems are only as reliable as the controls that govern them. When those controls fail, the consequences extend beyond lines of code to issues of trust, privacy rights and organisational resilience. As AI continues to weave into daily work and governance, organisations must be vigilant, proactive and transparent in how they harness these technologies. The goal is not to reject innovation but to ensure that innovation operates within frameworks that protect users and uphold the highest standards of data protection.

Senior Reporter/Editor
Bio: Ugochukwu is a freelance journalist and Editor at AIbase.ng, with a strong professional focus on investigative reporting. He holds a degree in Mass Communication and brings extensive experience in news gathering, reporting, and editorial writing. With over a decade of active engagement across diverse news outlets, he contributes in-depth analytical, practical, and expository articles exploring artificial intelligence and its real-world impact. His seasoned newsroom experience and well-established information networks provide AIbase.ng with credible, timely, and high-quality coverage of emerging AI developments.